A SSH key is an access credential in the SSH Protocol. SSH keys offer a more secure way of logging into a server with SSH than using user and password. More over, using a SSH-Key gives you the possibility to automate the login process, meaning you could create a script that will login to another computer without user intervention. More info about SSH-Keys could be find here.
Let’s see how it’s working for Linux and after that we move to Windows.
Linux
We’ll call client the machine that initiates the login, and server the one that receives and accepts the SSH login.
Step One – Create the RSA Key Pair
On the client machine we’ll generate a SSH-Key pair using the command:
# ssh-keygen
Step Two – Save the Key Pair
You have the option to change the location and the name of the generated SSH-key pair or leave the default which is home directory of the user and the default name – id_rsa. We’ll leave it on default in this case.
You will be prompted for a passphrase, it is recommended to use it, but it’s not mandatory to insert one. If you press Enter you will ignore this question. We will not set a passphrase this time because we need to create an automate SSH-login.
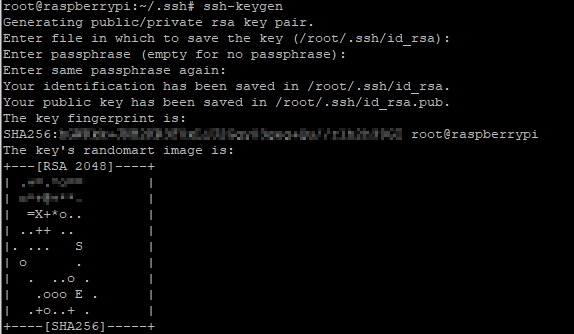
Step Three – Copy the Public Key
If we look now in ~/.ssh/, we’ll find the key pair: id_rsa is the private key and id_rsa.pub is the public key. We have to copy now the public key to the destination computer using the command:
# ssh-copy-id user@xxx.xxx.xxx.xxx
Replace user@xxx.xxx.xxx.xxx with the actual user and IP address of the server machine.
You will be asked for the password of the user account you are logging in to, in our case, user@xxx.xxx.xxx.xxx
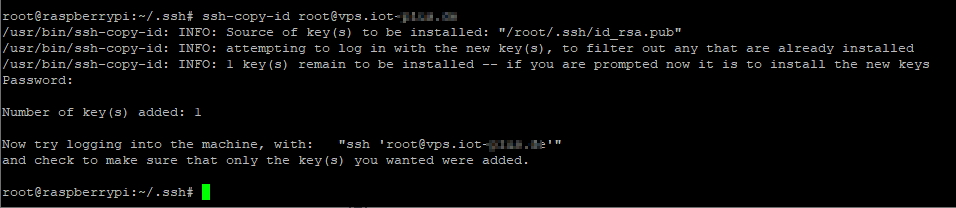
Because we are logged in with user root, the key has been copied to /root/.ssh/authorized_keys on the server machine.
If ssh-copy-id is not working, you can copy the public key using the folowing commands:
# cat ~/.ssh/id_rsa.pub | ssh user@xxx.xxx.xxx.xxx "cat >> ~/.ssh/authorized_keys"
Step Four – Connect to server machine without password
Now we can start the SSH connection from client machine to server machine without using a password.
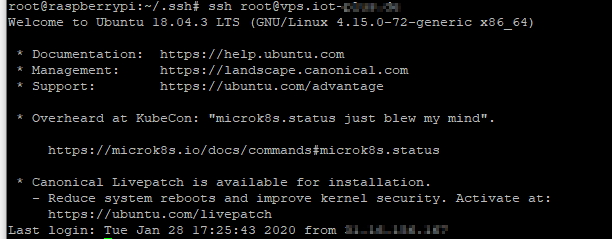
To give you a practical example, I’ve used a ssh-key based authentication login to implement an automatic Reverse SSH Tunnel from a Raspberry to a VPS. Raspberry would be the client machine that initiates the connection and it uses the privatekey, and VPS is the server machine which accepts the connection based on its public key.
More about configuring a Reverse SSH-Tunnel could be find here.
Windows
If we want to implement the same authentication on Windows, we can generate a ssh-key pair using PuTTY Key Generator. You can find it here.
Step One – Create the RSA Key Pair
After you start the application, you have to press the Generate button to create a pair of keys. Here is how it looks when the keys have been generated.
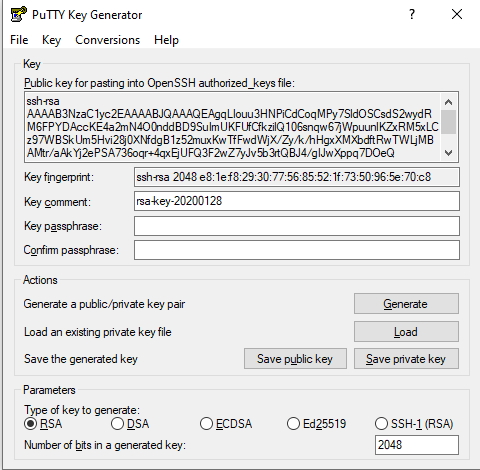
Step Two – Save the Key Pair
Press Save public key and Save private key to manualy save both keys to a secure place in the client machine.
Step Three – Copy the public key
Start Putty and connect to the server machine. Use the user and the password to login and copy the public key in the ~/.ssh/authorized_keys file.
Step Four – Connect to server machine without password
After that you can configure Putty to connect to the destination computer using ssh-key based authentication. Select the private key as you see below.
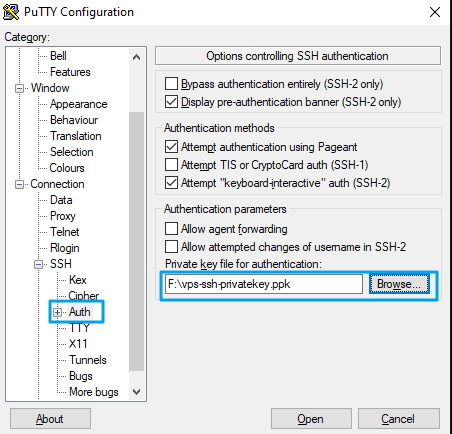
Starting from now you will not need to use the password anymore, the login will be done, without the password.